Take Down a Website from Your Cellphone - Dream Tool for an Hacktivist
Mobile LOIC
Mobile LOIC is the online web version of LOIC. It is
a Javascript-based HTTP DoS tool that is delivered within an HTML page, has very
few options and is limited to conducting HTTP floods. Unlike its PC counterpart,
Mobile LOIC does not support more complex options, like randomization of URLs
and remote control by IRC botnets (“the Hive”).
 Mobile LOIC is flexible
because it can run on various browsers and be accessed remotely. Typically,
attack organizers post a URL for the website hosting the page and invite others
to use the tool to attack the specified target. Since only a web browser is
required, an attacker can use a smartphone to generate an attack.
Mobile LOIC is flexible
because it can run on various browsers and be accessed remotely. Typically,
attack organizers post a URL for the website hosting the page and invite others
to use the tool to attack the specified target. Since only a web browser is
required, an attacker can use a smartphone to generate an attack.
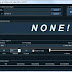
Offering extremely simple operation, Mobile LOIC has only three configuration parameters:

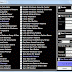
Recently, a new variant of the Mobile LOIC was detected, which incorporates several techniques to bypass detection and provide greater redundancy. These include:
hack a website from cell phone, cellphone website hack, hacktivism protest cellphone :Search tags:
 Mobile LOIC is flexible
because it can run on various browsers and be accessed remotely. Typically,
attack organizers post a URL for the website hosting the page and invite others
to use the tool to attack the specified target. Since only a web browser is
required, an attacker can use a smartphone to generate an attack.
Mobile LOIC is flexible
because it can run on various browsers and be accessed remotely. Typically,
attack organizers post a URL for the website hosting the page and invite others
to use the tool to attack the specified target. Since only a web browser is
required, an attacker can use a smartphone to generate an attack.Offering extremely simple operation, Mobile LOIC has only three configuration parameters:
- Target URL - the URL of the attacked target. Must start with http://
- Requests per second - the number of desired requests to be sent per second
- Append message - the content for the message parameter to be sent within the URL of HTTP requests
- Consisting of simple 100 lines of code that execute web requests in a loop. It is possible to append text with an appropriately revolutionary message.

Recently, a new variant of the Mobile LOIC was detected, which incorporates several techniques to bypass detection and provide greater redundancy. These include:
- A JavaScript method that prevents left mouse click in order to prevent users from viewing the page source code.
- Obfuscating all JavaScript methods contained and referenced on page, which may slow down security researchers from fully investigating this tool and its capabilities.
- Removal of a message field that existed in the original version and had its value included in the attack packets themselves. This is most likely in order to try and avoid signature based protections.
- Links from each attack page to up to 4 mirror attack pages hosted on other servers in order to quickly reference users and allow the attack campaign to continue even if one or more of the mobile LOIC nodes are taken down.
- Additionally, several “cosmetic” functionalities were also added such as listing the number of current attackers using the tool, and reflecting the current client IP detected by the tool which may prove useful when trying to avoid attacks using an attackers real IP address.
hack a website from cell phone, cellphone website hack, hacktivism protest cellphone :Search tags:








![Windows 10 Permanent Activator [Direct Download]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhjnKh-GcPJIcmGZmULqpAQCPQSOqh_wXmErNz36G87rmywQIO3kRpCxsYu-_d-9qxdsQiqS2Qpu_Q3N5yXHZ_aq_SE8P1LgoIJyYznfJ3km6QguvR47B-1m2QNYLkrRtrLwvN5vP91m6c/s72-c/windows-10-permanent-activator-ultimate.png)

![YouTube By Click 2.2.78 + Crack [Torrent Download]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgZ61nEDngG9b9yhUK7S8KkEW3A7wquCuS7neIHelko7E58OgOb-LgONBFBPzdtj4SvMj3GBZlws-st_sqnLIPyxae_kyYgwMa8GT1gIlh4GUrZk7GEDJb12gNaEzFYfpjrT2fXtIAPs3M/s72-c/th_XYne_Tml_LPDkj_JWCj_Ne_Bl_Fq_BOOwq4y8uv.png)






http://mobileloic.webs.com/ (dead link) please update this one. tnx in advance
ReplyDelete◾PROTOCOL SHIELDERS◾
DeleteHELLO, I am COREY RODRIGUEZ by name,the only CEO of protocol-cyber-shield-hackers. In this message, we will explain how you can almost avoid SCAMMERS and stay safe, plus how our organization works. Read it carefully!! Its reading will not take more than 10mins.
We kindly URGE you to not respond without have read the entire text. Those who mail without have read everything, ask questions that are been answered here.
⚠️WARNING:
MOST HACKERS YOU SEE HERE ARE FAKES AND SIMULTANEOUSLY INCONGRUOUS !.
It tears US up when we receive bitter mails of Jobs attempts proposals from most clients with hacking issues but never get close to having them done, thereby wasting a lot $ in the process,
EXAMPLES:
➡️MOBILE PHONE HACKING.
➡️BINARY FUNDS/BITCOIN RECOVERIES.
➡️SOCIAL MEDIA ACCOUNT HACKING etc....
if you in a haste to have all of these done by seeking hackers yourselvesyou will only get ripped.
PLEASE PAY ATTENTION TO THIS ARTICLE AS YOU READ THROUGH IT.
HOW WOULD YOU KNOW??
TAKE NOTE AND PRECAUTIONS:
1. you see uncertified email accounts carrying numberings likeiamhacklord1232@(gmail,yahoo or hotmailDOTcom) pls flee from them, BIG SCAMMERS.
They take your money and never do your job!!
2. you see posts like "do you need to spy on spouse?" All fake!just a way to lure you towards getting ripped!. 3, posting fake testimonies and comments to trick you into feeling safe. Pls endeavour to ignore!!
➡️NOTE: beware as we urge you not to make respond to any "IVAN HONG,PETER SANTOS,MONICA HART (impersonating with our articles pretending to work under us)
WE ONLY HAVE 2 EMAILS WHICH ARE LISTED BELOW THIS ARTICLE TO ATTEND TO ALL MANNERS OF CYBER HACKING ISSUES.
◾VERY IMPORTANT ◾
For years now, We've helped organizations secure data base, so many sites USE US AS SECURITY BACK UP TEAM BECAUSE OF OUR METHODS OF HANDLING CYBER MISHAPS.
"iPhone/ANDROID HACKS"
"CLEAR CRIMINAL RECORDS"
"FUNDS RECOVERIES" AND LOT MORE BEEN DONE IN SHORT TIMING!
these are significant EXPERIENCES & RECORDS a good and effectively fully recognized organization must firmly ascertain.
◾OUR AIMS HERE◾
1◾to assign a qualified agent of specific rank to particularly any sort of cyber issues you intend dealing with in short and accurate timing.
2◾ to screen in real hackers (gurus only) in need of job with or without a degree, to speed up the availability of time given for Job contracts given to us.!! Thus an online binary decoding exam will be set for those who seeks employment under the teams Establishment.
write us on:
◾Protocolhacks@gmail.com
◾Cybershieldnotch@gmail.com
◾binaryoptionretrieval@gmail.com
COREY ROD,
SIGNED...
Thank you..
◾PROTOCOL SHIELDERS◾
DeleteHELLO, I am COREY RODRIGUEZ by name,the only CEO of protocol-cyber-shield-hackers. In this message, we will explain how you can almost avoid SCAMMERS and stay safe, plus how our organization works. Read it carefully!! Its reading will not take more than 10mins.
We kindly URGE you to not respond without have read the entire text. Those who mail without have read everything, ask questions that are been answered here.
⚠️WARNING:
MOST HACKERS YOU SEE HERE ARE FAKES AND SIMULTANEOUSLY INCONGRUOUS !.
It tears US up when we receive bitter mails of Jobs attempts proposals from most clients with hacking issues but never get close to having them done, thereby wasting a lot $ in the process,
EXAMPLES:
➡️MOBILE PHONE HACKING.
➡️BINARY FUNDS/BITCOIN RECOVERIES.
➡️SOCIAL MEDIA ACCOUNT HACKING etc....
if you in a haste to have all of these done by seeking hackers yourselvesyou will only get ripped.
PLEASE PAY ATTENTION TO THIS ARTICLE AS YOU READ THROUGH IT.
HOW WOULD YOU KNOW??
TAKE NOTE AND PRECAUTIONS:
1. you see uncertified email accounts carrying numberings likeiamhacklord1232@(gmail,yahoo or hotmailDOTcom) pls flee from them, BIG SCAMMERS.
They take your money and never do your job!!
2. you see posts like "do you need to spy on spouse?" All fake!just a way to lure you towards getting ripped!. 3, posting fake testimonies and comments to trick you into feeling safe. Pls endeavour to ignore!!
➡️NOTE: beware as we urge you not to make respond to any "IVAN HONG,PETER SANTOS,MONICA HART (impersonating with our articles pretending to work under us)
WE ONLY HAVE 2 EMAILS WHICH ARE LISTED BELOW THIS ARTICLE TO ATTEND TO ALL MANNERS OF CYBER HACKING ISSUES.
◾VERY IMPORTANT ◾
For years now, We've helped organizations secure data base, so many sites USE US AS SECURITY BACK UP TEAM BECAUSE OF OUR METHODS OF HANDLING CYBER MISHAPS.
"iPhone/ANDROID HACKS"
"CLEAR CRIMINAL RECORDS"
"FUNDS RECOVERIES" AND LOT MORE BEEN DONE IN SHORT TIMING!
these are significant EXPERIENCES & RECORDS a good and effectively fully recognized organization must firmly ascertain.
◾OUR AIMS HERE◾
1◾to assign a qualified agent of specific rank to particularly any sort of cyber issues you intend dealing with in short and accurate timing.
2◾ to screen in real hackers (gurus only) in need of job with or without a degree, to speed up the availability of time given for Job contracts given to us.!! Thus an online binary decoding exam will be set for those who seeks employment under the teams Establishment.
write us on:
◾Protocolhacks@gmail.com
◾Cybershieldnotch@gmail.com
◾binaryoptionretrieval@gmail.com
COREY ROD,
SIGNED...
Thank you..